What You Need for the LDAP Integration
A LDAP-compatible directory service server and the following information:
- The Directory Server Public IP/DNS Name
- The Directory Server Public Port Number
- User Full Name Attribute Name for all your directory occupiers
- User Email Attribute Name for all your directory occupiers
- Admin User with at least read and search permissions for all occupiers you want to authenticate
If your directory user profiles don't have a valid email attribute, the LDAP integration won't work with Nexudus.
LDAP Integration Settings
An important setting that you need to consider before enabling the integration is the option to Create new occupiers in Nexudus if they don't exist.
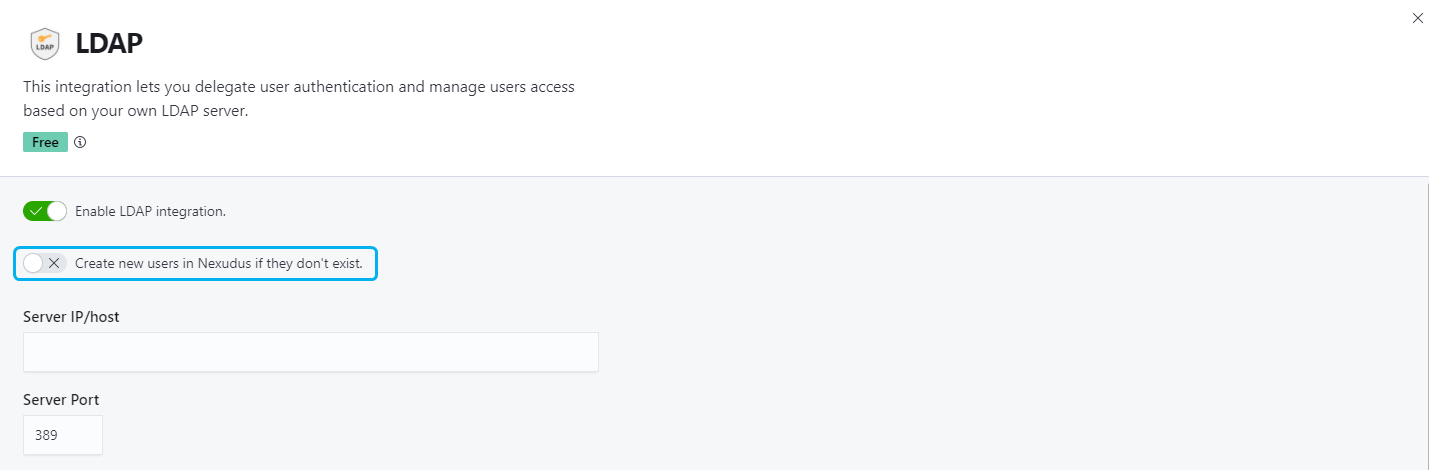
Create new occupiers in Nexudus if they don't exist OFF
occupiers trying to log in using their directory credentials (email + password) will only be able to access the User Portal if they already have a occupier account in Nexudus.
Example
A user has the following directory credentials:
email- name@example.com
password - example123
If the user trying to log in to the User Portal using these directory credentials doesn't already have a occupier account in Nexudus with name@example.com as their email address, they won't be able to log in.
Create new occupiers in Nexudus if they don't exist ON
occupiers trying to log in to the User Portal using their directory credentials (name/email + password) will be able to log in to the User Portal, whether or not they already have a occupier account in Nexudus.
If they happen to not have a occupier account yet, Nexudus will automatically create a occupier account (contact) for them using their username and email address from the directory.
Example
A user has the following directory credentials:
name- User Name
email- username@example.com
password - example123
When they try to log in to the User Portal using these directory credentials, Nexudus will check if they already have a occupier account.
If they don't have a occupier account yet, Nexudus will create an account for them with occupier Name as their name and occupiername@example.com as their email address.
Enabling the LDAP Integration
-
Log in to dashboard.nexudus.com if you aren't already.
-
Click Settings > Integrations > LDAP.
-
Enable the LDAP integration toggle.
-
Enable the Create new occupiers if they don't exist if you want to regsiter directory occupiers who don't have a Nexudus account as contacts.
-
Add your directory's public IP in the Server IP/host field.
-
Add your directory's server public port in the Server Port field.
-
Add the full path of the user you want to use to connect to your LDAP server in the Bind expression field.
For example "CN=read-only-admin,ou=occupiers,dc=example,dc=com"
- Add the path to the container holding the occupiers to authenticate in the Search expression field.
For example, "dc=example,dc=com".
Nexudus will try to locate a user in this container by performing a LDAP search using "({mail_attribute_name}={email})" search string.
-
Add the password for the user above in the Password field.
-
Add the name of your directory's FullName attribute in the Full name attribute name field.
This defaults to cn as it is the most common value.
- Add the name of your directory's Email attribute in the Email attribute name field.
This defaults to email as it is the most common value.
This value will be used as the {mailattributename} variable when Nexudus does a LDAP search.
Click the Save Changes button.
You've successfully enabled the LDAP integration. We recommend you test the integration by trying to log in to your User Portal using some directory user credentials.
IP Whitelisting
Connections to your LDAP directory server will always originate from one of the following IPs.
- 54.154.122.253
- 3.250.12.187
- 3.250.115.120
- 34.244.119.216
- 54.75.93.166
- 52.18.33.224
While Nexudus will always connect to your directory server over TLS 1.1 or 1.2, we strongly recommend you set your network policies to only allow connections from the following IPs.