What You Need to Integrate RADIUS
-
A Controller Supported by IronWifi
IronWifi is the provider that we use to issue RADIUS licenses. You need to ensure your Wi-Fi controller is compatible with IronWifi to enable the integration.
For more details, check out IronWifi's list of supported controllers.
-
A RADIUS License
Nexudus needs to issue a RADIUS license for you before enabling the integration on the Admin Panel.
Each additional access point costs $/£/€6 per month.
If you haven't requested a RADIUS license yet, contact support and let them know the number of access points you have and your controller's vendor name.
Once you receive an email confirmation from our support team, you can move to the integration process.
Integrating RADIUS
Once you have the RADIUS license set up in your account, all you need to do is configure your access points following IronWifi's instructions.
Log in to dashboard.nexudus.com if you aren't already.
- Click on Configuration sheet.
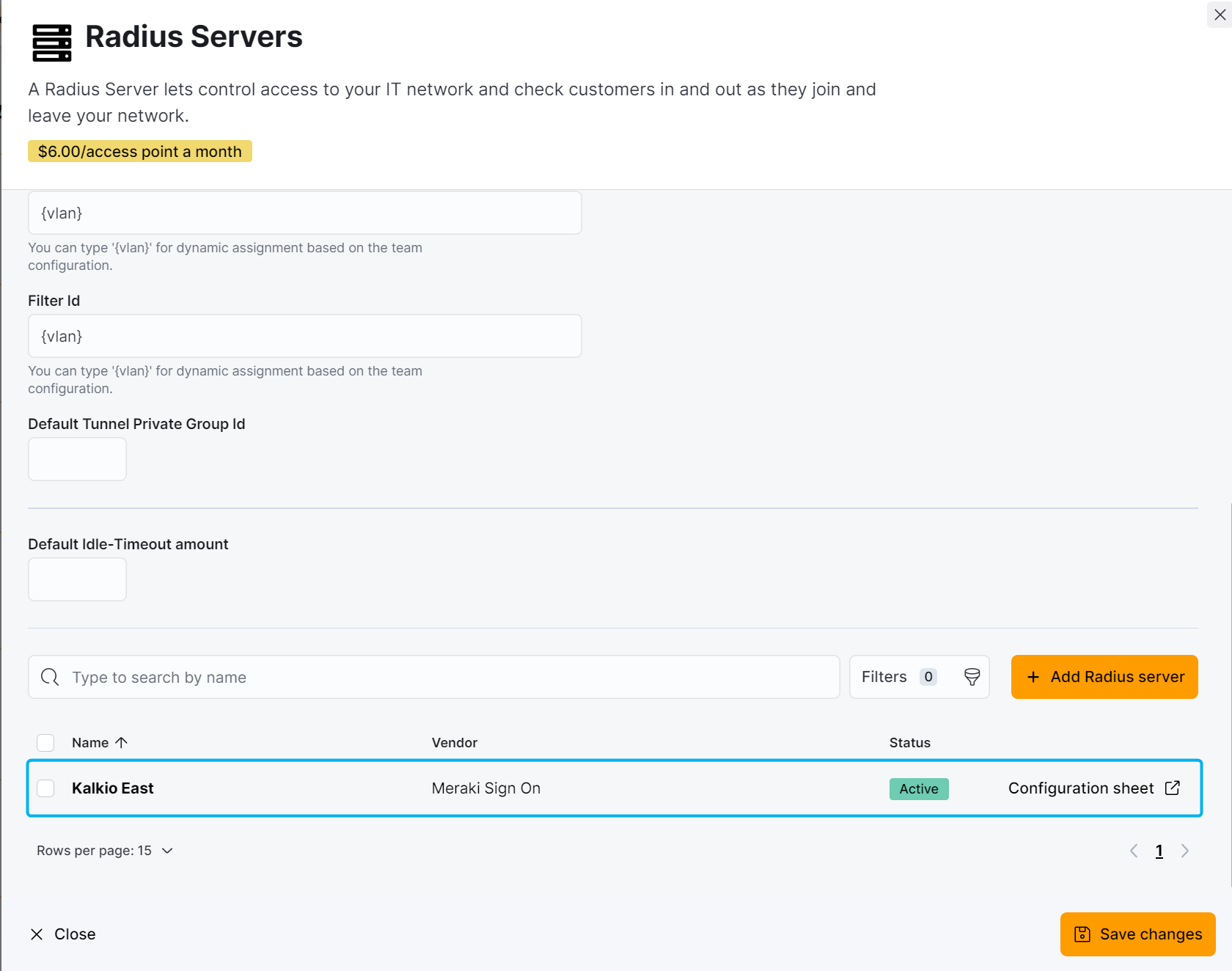
You're redirected to an IronWifi page containing instructions on how to set up your access points for Nexudus.

The instructions are automatically adjusted based on the controller vendor you use.
Simply go to your controller and follow the instructions provided on the IronWifi page. You're ready to go once you've set up all your access points.
Follow our Ruckus Controllers Setup instructions as well.
Your RADIUS integration is now complete. We recommend you check the setup by trying to log in to your Wi-Fi network as a customer.